Grindr, one of the world’s largest dating and social networking apps for gay, bi, trans, and queer people, has fixed a security vulnerability that allowed anyone to hijack and take control of any user’s account using only their email address.
Wassime Bouimadaghene, a French security researcher, found the vulnerability and reported the issue to Grindr. When he didn’t hear back, Bouimadaghene shared details of the vulnerability with security expert Troy Hunt to help.
The vulnerability was fixed a short time later.
Hunt tested and confirmed the vulnerability with help from a test account set up by Scott Helme, and shared his findings with TechCrunch.
Bouimadaghene found the vulnerability in how the app handles account password resets.
To reset a password, Grindr sends the user an email with a clickable link containing an account password reset token. Once clicked, the user can change their password and is allowed back into their account.
But Bouimadaghene found that Grindr’s password reset page was leaking password reset tokens to the browser. That meant anyone could trigger the password reset who had knowledge of a user’s registered email address, and collect the password reset token from the browser if they knew where to look.
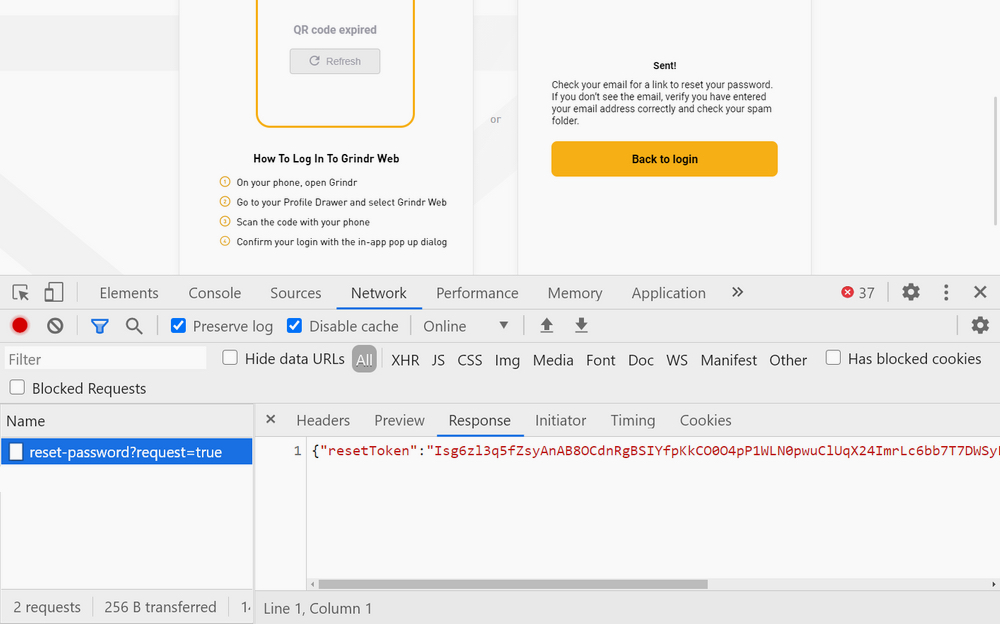
Secret tokens used to reset Grindr account passwords, which are only supposed to be sent to a user’s inbox, were leaking to the browser. (Image: Troy Hunt/supplied)
The clickable link that Grindr generates for a password reset is formatted the same way, meaning a malicious user could easily craft their own clickable password reset link — the same link that was sent to the user’s inbox — using the leaked password reset token from the browser.
With that crafted link, the malicious user can reset the account owner’s password and gain access to their account and the personal data stored within, including account photos, messages, sexual orientation and HIV status and last test date.
“This is one of the most basic account takeover techniques I’ve seen,” Hunt wrote.
With a leaked password reset token, an attacker could reset a user’s password, hijack their account and access their private data. (Image: Troy Hunt/supplied)
In a statement, Grindr’s chief operating officer Rick Marini told TechCrunch: “We are grateful for the researcher who identified a vulnerability. The reported issue has been fixed. Thankfully, we believe we addressed the issue before it was exploited by any malicious parties.”
“As part of our commitment to improving the safety and security of our service, we are partnering with a leading security firm to simplify and improve the ability for security researchers to report issues such as these. In addition, we will soon announce a new bug bounty program to provide additional incentives for researchers to assist us in keeping our service secure going forward,” the company said.
Grindr has about 27 million users, with about 3 million using the app every day. Grindr was sold earlier this year by its former Chinese owner, Beijing Kunlun, to a Los Angeles-based company said to be led largely by Americans, following accusations that the company’s Chinese ownership constituted a national security threat.
Last year, it was reported that while under Chinese ownership, Grindr allowed engineers in Beijing access to the personal data of millions of U.S. users, including their private messages and HIV status.
You can send tips securely over Signal and WhatsApp to +1 646-755-8849 or send an encrypted email to: zack.whittaker@protonmail.com
from Microsoft – TechCrunch https://techcrunch.com/2020/10/02/grindr-account-hijack-flaw/
No comments:
Post a Comment